Security firm FireEye has recently uncovered a new kind of Android malware, one that doesn’t show you ads or install junk apps; rather it mimics the look and feel of your most trusted apps.
Imagine you see a prompt from Google Play store to login again as your session has expired. What would you do? login again and provide your credentials, right?
But what you didn’t know, it wasn’t Google asking you to re-verify, but the nasty overlay malware which now has your precious password.
How it Works?
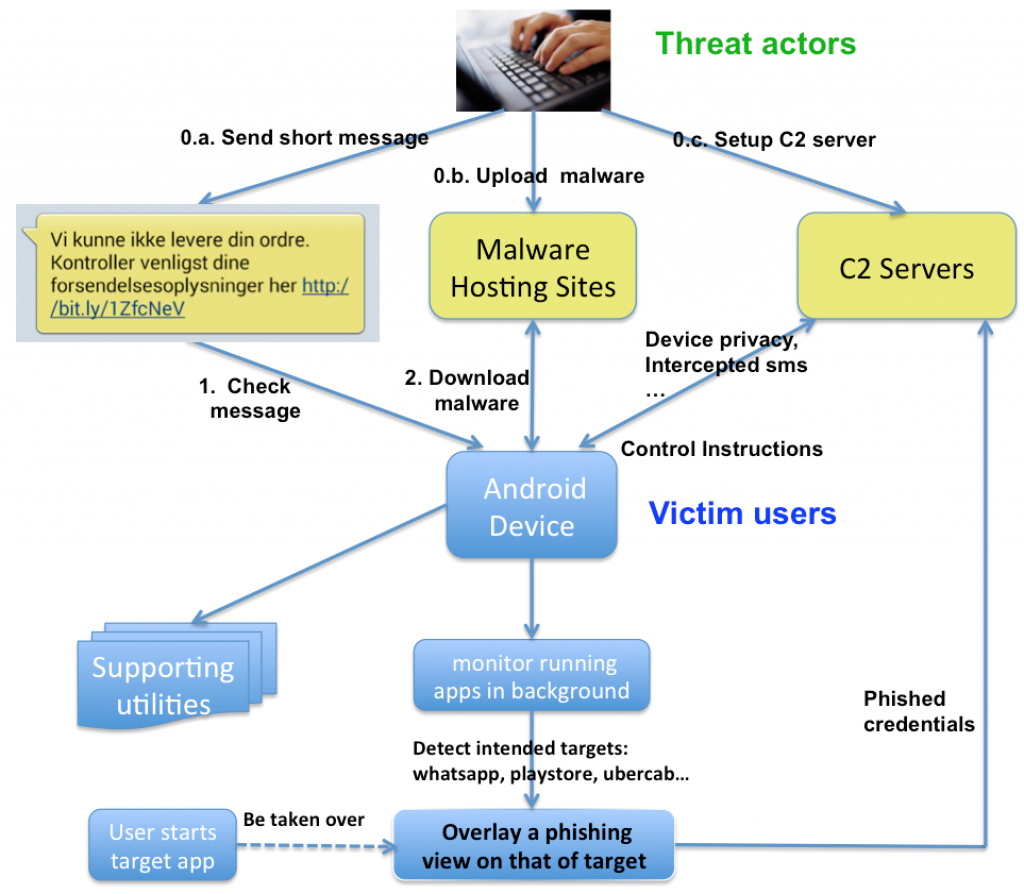
According to research team, this malware is spread by a basic SMS phishing scheme. The user receives message and subsequently clicks on an ostensibly legit link.
The malware is downloaded quietly and begins to monitor which apps are active and which apps are running in the background.
Using overlay techniques it present a nearly identical credential input UIs as seen in benign apps, subsequently tricking unwary users into providing their secure credentials.
The victims never know about this attack because they trust the UI screen in front of them, that popped up because they launched a trusted application.
Authors of this particular malware are getting more sophisticated by sending out enticing links via SMS, like “We couldn’t deliver your order, please update your shipping information by clicking here.”
The overlay malware can mimic several apps, including WhatsApp, WeChat, Uber, Facebook, Viber and Google Play.
How to Protect Against the Malware?
To protect against these threats, it is recommended not install apps from outside official app stores, and take caution before clicking any links where the origin is unclear.
Do install an antivirus application in your mobile as well and try keeping all of your applications up to date.