For almost a decade a vulnerability in Intel chips that went undiscovered, that allows hackers to remotely gain full control over affected Windows PCs without needing a password or physical access.

This bug was disclosed last week which affects, Intel’s Active Management Technology (AMT), used by IT administrators to remotely carry out maintenance and other tasks on entire fleets of computers as if they were there in person.
AMT which is also available through a web browser allows the administrator to remotely control the computer’s keyboard and mouse and they can turn on the computer if its in sleep mode.
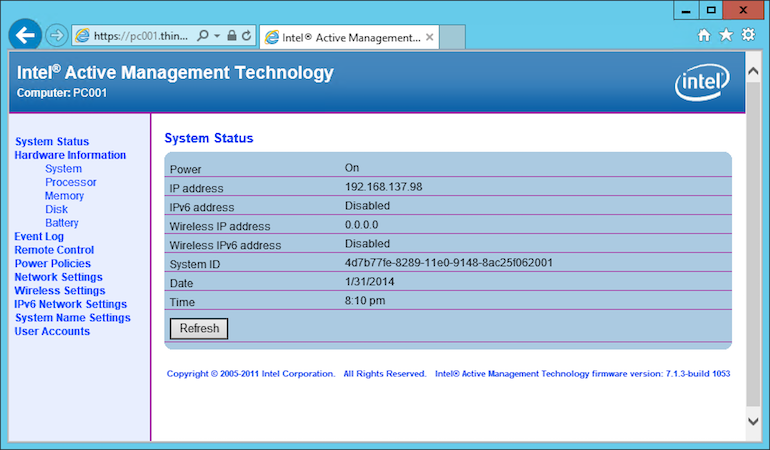
Embedi researchers, credited with finding the bug, notes that a flaw in how the default “admin” account for the web interface processes the user’s passwords effectively lets anyone log in by entering nothing at the log-on prompt.
Intel says that systems, including desktops, laptops, and servers dating back as early as 2010 and 2011 are affected by the flaw. The company said that it’s working with its hardware partners to address the problem and soon updates will be rolled out to fix this bug. In the meantime you can use this tool to find if your computer is affected or not.



